

With Teaboard, which also comes with a LAN connector, in addition to several I/O terminals for I/O use (GPIO) plus two serial channel connectors that can be used as digital input/output (DIO), a wide range of applications in equipment control use are also possible. As one application of that type, we developed a system that manages room entrance and exiting by controlling the electric lock of an office door with Teaboard, based on combination with an individual authentication system that uses eTRON cards.
In this article, in regard to the electric lock control system to which we applied Teaboard, we will report on development details, centering on such things as the configuration and operation of the system, and its relationship to the eTRON card. Furthermore, this system is one that began actual practical use in an office at a certain location in Tokyo from September of this year.
We use Teaboard for the control board of this system overall, but outside of that, an electric lock (a lock that can be unlocked electrically) that will be built into the actual door and an electric lock control board that will its controller will also be necessary. As for these these devices, because ready made goods for business use are commercially available, we will utilize those.
Various options are available among commercially available electric locks and controllers, and when you connect them, it is possible to realize functions such as unlocking by means of inputting a personal identification number from a 10-key keypad, or unlocking with remote control from a control board. However, in the system on this occasion, we will not be using these types of optional parts, rather we will utilize an eTRON non-contact IC card that can also double as an employee identification, and thus we will realize a high-level office entrance and exit management functions, beginning with unlocking at the time of entrance.
 |
|
|
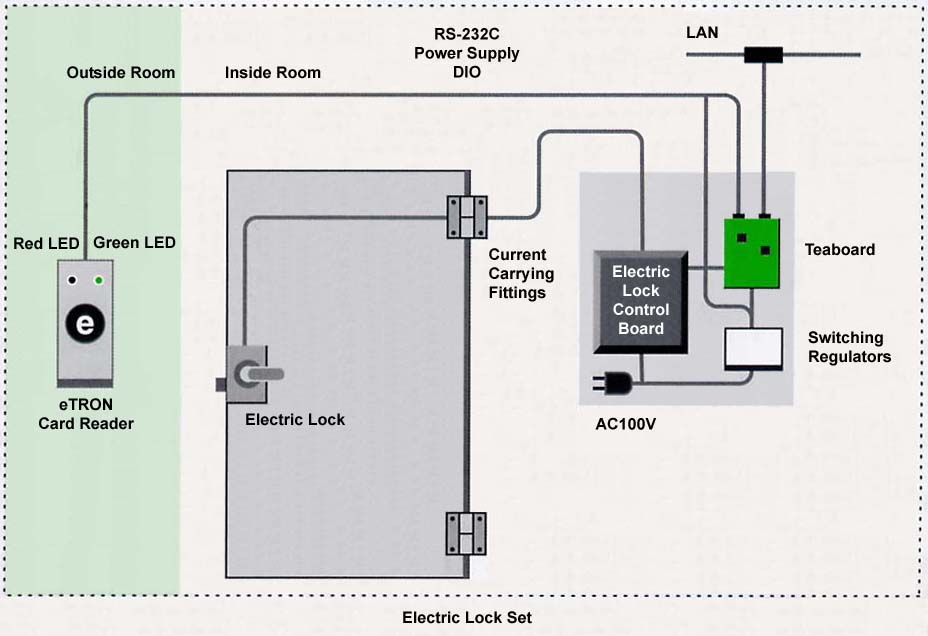
We show in Fig. 1 the hardware configuration of this system. Furthermore, in order to make the explanation easy to understand, in this figure, we have pulled out only the necessary parts for the propose of controlling on lock. Below, we will explain the details of each component of the hardware configuration.
 |
|
|
Electric Lock
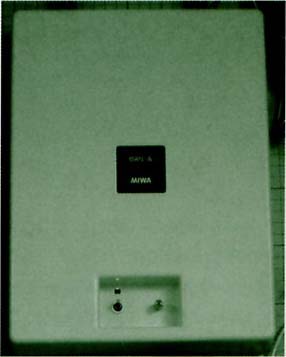
There are various types among commercially available electric locks, but for the system on this occasion, we selected and utilized an electric lock (Fig. 2) that satisfied the following requirements.
 |
|
Electric Lock Control Board
In regard to the electric lock control board also, there are various types of products that are on sale, and one selects by also taking into consideration the number of electric locks that will be used. In the system on this occasion, because we would use multiple electric locks, we made use of an electric lock control board (Fig. 3) compatible with that. The electric lock control board possesses the following inputs and outputs.
In this system, we carry out control of the lock by connecting to Teaboard's I/O terminals timer input, warning output, door opening output, and unlocking output, among those mentioned above.
eTRON Card and Card Reader
What we call eTRON is a security architecture developed as a part of the TRON Project, and it can be utilized in a wide variety of applications, such as electronic money, electronic tickets, individual authentication, and DRM (Digital Rights Management).
The eTRON card that we are using in this system is one eTRON application product; it is an ISO14443-based non-contact IC card the size of a business card. Because it is also possible to carry out printing on top of an eTRON card using a special printer, printing such things as facial photographs, names, and company logos, and then putting it into practical use as an employee identification is also possible. In other words, eTRON cards distributed to each employee can serve both as a key for entering the office and as an employee identification.
 |
 |
|
|
|
|
|
|
There are also various types of card readers that read out data by carrying out non-contact communication with the eTRON card, but on this occasion, we have utilized a card reader (Fig. 4) that possesses an RS-232C interface. Accordingly, the the signal line from the card reader is connected to Teaboard's RS-232C connector (serial port). The card reader communicates with the eTRON card using the 13.56 MHz carrier frequency by means of the ISO14443 standard.
 |
|
LED for Confirmation Use of Authentication Status
So that one can discern by seeing with the eye the pro or con of authentication of the eTRON card, we installed green and red LEDs close to the card reader (Fig. 5). In a case where the authentication is successful and the door has unlocked, the green LED lights up, and in a case where the authentication is unsuccessful and the door hasn't unlocked (an improper eTRON card was used), the red LED lights up.
These LEDs connect to the Teaboard's GPIO (DIO); in order to drive the LEDs, we have inserted a buffer between Teaboard and the LEDs.
Connecting with Teaboard
In the electric lock control system on this occasion, among Teaboard's abundant I/O functions, we have used the following I/O functions.
|
For connection use with the eTRON reader |
|
For connection use with the LEDs used for confirming the authentication state (green or red) |
|
Used to output the unlock signal |
|
Used to input the unlock signal, the door opened signal, and the warning signal |
|
|
In regard to the details of the Teaboard hardware specification, we yield to other articles, but what we have utilized in this system is a small portion of Teaboard's I/O functions. Because many unused I/O functions, such as another RS-232C and numerous GPIO (DIO), also remain, realizing a higher level system by making use of these I/O functions is also possible.
 |
|
|
Power Supply Circuits
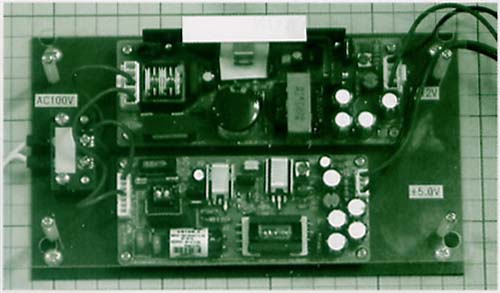
With the power supply circuits (Fig. 6), we supply electrical power to Teaboard and the eTRON card reader. Because it is necessary to provide a power supply of 5 Volts to Teaboard and 12 Volts to the eTRON card reader, we have used two types of switching regulators.
Higher Level Server
By connecting via a LAN with a higher level server machine that uses UNIX or Windows, we have realized higher level entrance and exit management functions, such as downloading of authentication information and log management. We will explain the details in the next section.
In the electric lock control system, we judge whether or not to carry out the unlocking of the door based on data from the eTRON card that is held over the card reader. Accordingly, it is necessary to collect and preserve for future use on the Teaboard side data concerning the eTRON cards that permit the unlocking. These data are downloaded via a LAN from the higher level server at the time Teaboard's power supply is turned on and the program has started up. In a normal case, we commence operation of the electric lock control system on the basis of eTRON card authentication data newly acquired from the higher level server in this manner.
However, in a case where there has been some sort of problem on the LAN or higher level server side and this downloading wasn't possible, we commence operation of the system on the basis of data downloaded on the previous occasion that has been preserved in storage (SD card) on the Teaboard side. With a form of this type, we carry out schemes that raise the availability of the system.
Conversely, in a case of the type where there have been changes to the eTRON card authentication data placed on the higher level server side, even if there is a state in which the Teaboard side program is in the middle of executing, forcibly downloading to the Teaboard side the eTRON card authentication data after the changes and switching to operation with the new data is possible. This is a function to utilize the system in a case of the type where one has increased or decreased eTRON cards that are keys used for entrance.
The basic operations at the time of door unlocking by means of this system are the following. First, when one holds an eTRON card over the eTRON card reader, the data inside the eTRON card are read in. The program inside Teaboard compares the authentication data that have been downloaded beforehand from the higher level server and the data that have been read in from the eTRON card, and then it judges whether or not the eTRON card is a proper one, and whether or not it's all right to unlock the door. In a case where card authentication is successful, and it has been judged that the card is an proper one, the program lights up for a fixed period of time the green one of the LEDs used to confirm the authentication state, and together with that it simultaneously unlocks the door. On the other hand, in a case where there has been a failure in authentication, in other words in a case where it has been judged that a card is not a proper one, the program lights up the red one among the LEDs used to confirm the authentication state, which are installed beside the eTRON card reader, and then it informs the owner of the card that the door cannot be unlocked.
After the door is unlocked, when one closes it after opening it once, it is automatically locked again. Also, after the door is unlocked, even in a case where the door hasn't been opened but a fixed period of time has elapsed, the door automatically locks again. The electric lock control board automatically carries out these locking operations.
Outside of this, the system is set up so that during operation it supervises the results of eTRON card reader readout, and thus it records as a log data about such things as when the system permitted the unlocking of the door, or when authentication didn't succeed and the system didn't unlock the door.
In an electric lock control system using Teaboard and eTRON cards, outside of basic operations of the type explained in the previous section, it is also possible to realize the following types of functions by making use of the flexibility of eTRON.
Time Limited Key
If we make use of the eTRON card, realizing keys with which it is possible to enter only during a fixed time for part-time work use, or realizing keys that are valid only on a certain date, a certain day of the week, or during a certain period are easily possible.
Multiple Door Selection Key
In a case where there are multiple doors and rooms, it is possible to set the door(s) that can be unlocked for each eTRON card. Whether making it possible for the employee of a certain department to enter only this room and this room, or making entrance possible only to the reception room with an eTRON card lent out for visitor use, you can realize finely detailed office entrance management. Combination with the functions of the previously mentioned time limited key is also possible.
Invalidation of Lost Keys
In a case of the type where someone has lost an eTRON card, we can change the eTRON card authentication data placed on the higher level server side, invalidate the key function of the lost eTRON card, and thus avoid the situation of a person who obtained that illegally trespassing into the office (at this time, we utilize the previously mentioned forcible downloading function of eTRON card authentication data).
Furthermore, if you try the same support in a case where a person has lost a physical key, because it becomes necessary to change even the lock attached to the door, you cannot but also exchange all the keys that other people possess, and thus things become fairly troublesome.
Management of an Entrance and Exit Log
The carrying out of entrance and exit log management of eTRON card holders is possible by sending to the higher level server and preserving there the log data of unlocking. This function can be utilized for the purpose of making a record of, for example, when who entered a room that is important in terms of security. Recently, in particular, this type of function is important also from the viewpoint of the protection of personal data.
Because Teaboard is standard equipped with abundant I/O, such as DIO, RS-232C, and LAN, applying it to control use for facilities equipment, such as an electric lock control system and an office entrance and exit system is also easy. By means of the development example mentioned in this article, this point has been has been verified, and we were able to show the high-level capabilities that Teaboard potentially possesses. Furthermore, because the price of the board is cheap, there is also the merit that the system in its entirety can be constructed at low cost.
| Personal Media Corporation also carries out commissioned development of Teaboard application systems of the type explained in this article. Please feel free to make inquiries at Personal Media's T-Engine Sales Department (telephone: 03-5759-8305; e-mail: te-sales@personal-media.co.jp). |
The above article on Teaboard appeared on pages 69-73 in Vol. 95 of TRONWARE. It was translated and loaded onto this Web page with the permission of Personal Media Corporation.
Copyright © 2005 Personal Media Corporation
Copyright © 2009 Sakamura Laboratory, University Museum, University of Tokyo